Implement an iOS app protection policy
To create an iOS app protection policy, use the following procedure:
- Navigate to the Microsoft Endpoint Manager admin center and sign in using your global admin account.
- In the navigation pane, select Apps.
- In the Apps blade, under Policy, select App protection policies.
- Select Create policy.
- In the Create policy drop-down list, select iOS/iPadOS.
- On the Basics tab, enter the following information, and then select Next:
- Name Enter a name for your new policy.
- Description Enter an optional description.
7. On the Apps tab, displayed in Figure 4-40, configure the following information, and then select Next:
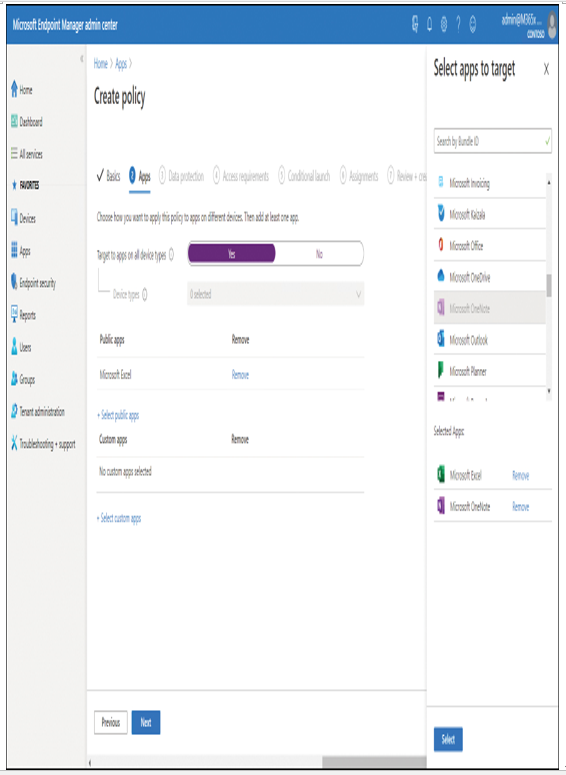
Figure 4-40 Specifying the apps to be protected in an app protection policy
- Target to apps on all device types Choose Yes or No. If you select No, then select either Unmanaged or Managed in the Device types drop-down list. A managed device is enrolled in and managed by Intune, whereas an unmanaged device is not enrolled, or else managed by an MDM other than Intune.
- Public apps Select the Select public apps link, and on the Select apps to target blade, select one or more apps for protection, and then click Select.
- Custom apps Select the Select custom apps link, and on the Select apps to target blade, search for and select the custom apps by entering a Bundle ID, and then click Select. For example, to add a custom app from Contoso, enter the Bundle ID of com.contoso.app.
8. On the Data protection tab, displayed in Figure 4-41, you configure the DLP settings (such as Cut, Copy, Paste, and Save As restrictions). Settings include:
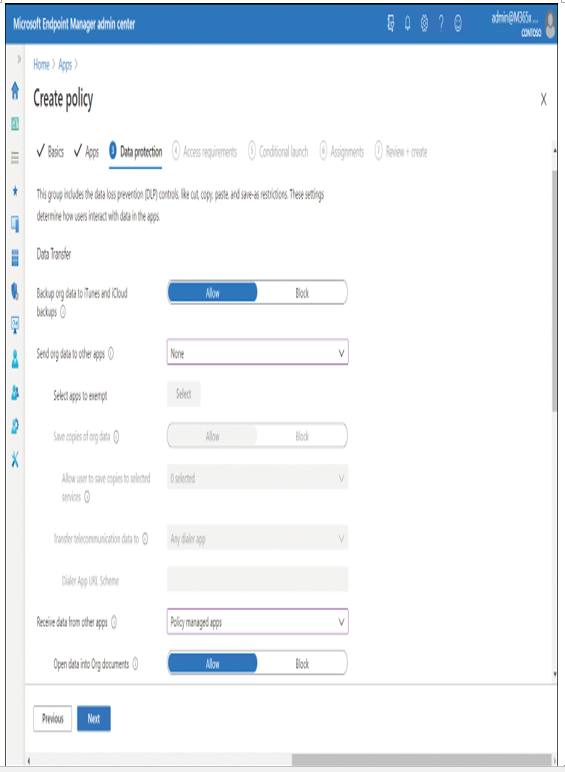
Figure 4-41 Configuring app protection policy data protection settings
- Data Transfer Controls whether or not users can send data from protected apps to other locations, such as iTunes and iCloud backups, and other specific apps. You can also control whether other apps can send data to the protected apps.
- Encryption Enables you to specify whether organizational data must be encrypted.
- Functionality Controls aspects of app usage with protected data, such as printing and synchronization.
9. Select Next, and then, on the Access requirements tab displayed in Figure 4-42, configure the PIN and credential requirements that users must meet to access apps in a work context. Then select Next.
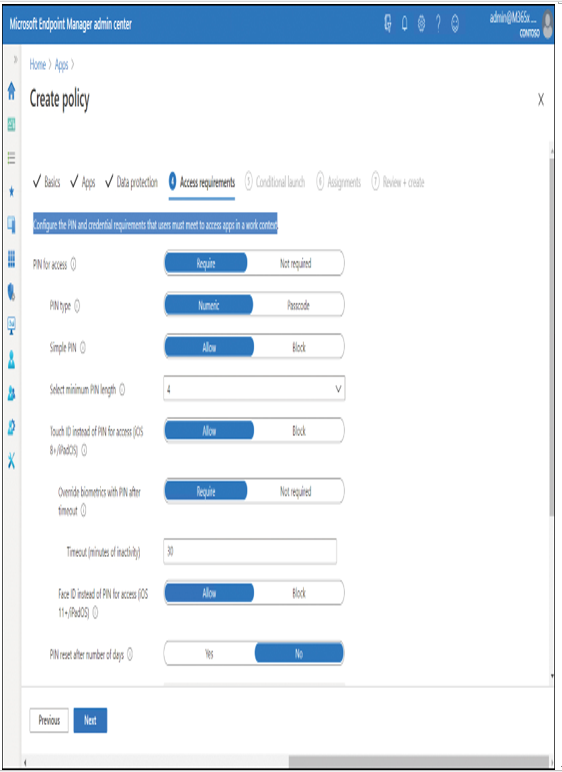
Figure 4-42 Configuring access requirements for an app protection policy
10. On the Conditional launch tab, displayed in Figure 4-43, you can define the following:
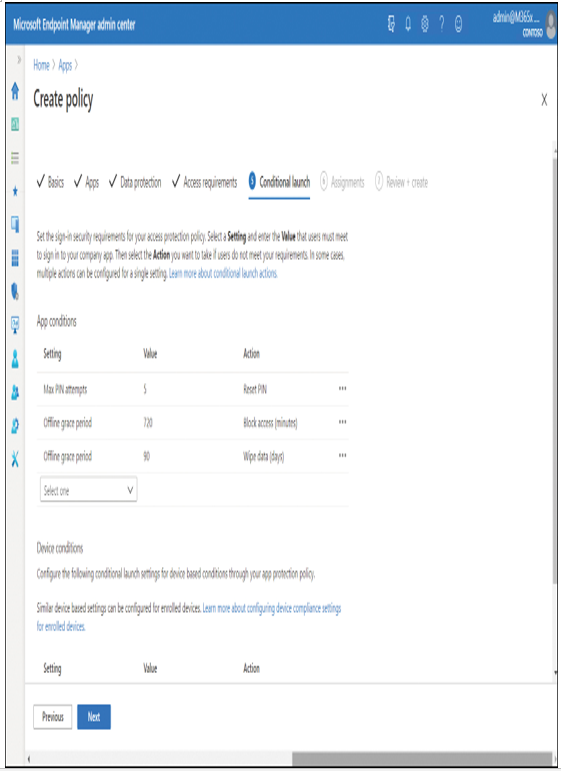
Figure 4-43 Defining the conditional launch setting in an app protection policy
- App conditions Defines actions taken when maximum PIN attempts are reached, or the action that is taken when a device is offline for more than a defined grace period. Actions include Reset PIN, Block access, and Wipe data.
- Device conditions Determines whether you’ll allow devices to launch protected apps if they are rooted (also known as jailbroken).
- Select Next. You must now assign the policy to group(s), as described in the “Create and manage groups for app assignment” section, earlier in this chapter.
- Select Next, and then select Create.